VPN Switcher
Targets of this project
The project should allow any device on my network to easily switch between multiple VPN networks. To achieve this I have decided to use a raspberry pi as a VPN gateway. For easy switching I am adding simple switches. Like this:
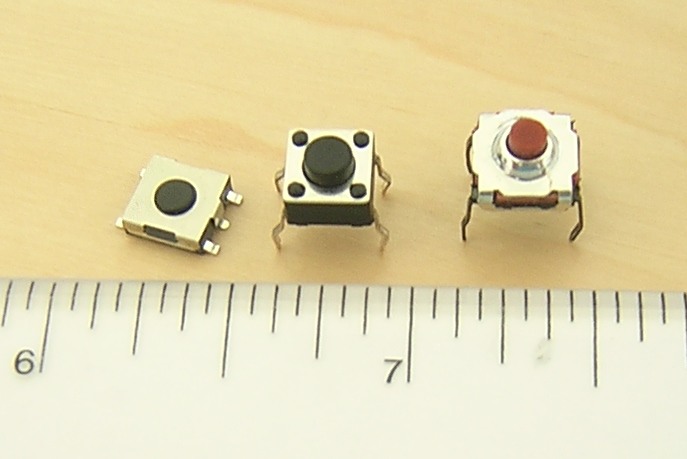
In the first part I will cover the software side of this project before I talk about simplifying the switching of the vpns with hardware buttons. The Software I will be using for this project are:
- openvpn
- squid
- bind9
- python
Preparing
To prepare the pi we have to install some packages: apt-get install openvpn squid3 bind9
- openvpn is used for our VPN connections
- squid3 is our proxy server
Here the python stuff we need apt-get install python python-pip pip install requests
Openvpn
Here we have to put the VPN Configuration files from our provider in the “/etc/openvpn/” folder. Each config file must also be edited to allow the forwarding and the authorization.
For the forwarding add the lines:
up /etc/openvpn/update-resolv-conf
down /etc/openvpn/update-resolv-conf
redirect-gateway
For the authentication I use the a central file which you can specify with this line:
auth-user-pass /etc/openvpn/user.txt
This file contains the user name in the first line and the password in the second line.
Bind9
Bind9 is our dns server to which we use to circumvent location blocking via the given dns server.
The important bind9 config is “/etc/bind/named.conf.options” here we add under “forwarders” the DNS server ips from our VPN provider.
options {
directory "/var/cache/bind";
// If there is a firewall between you and name-servers you want
// to talk to, you may need to fix the firewall to allow multiple
// ports to talk. See http://www.kb.cert.org/vuls/id/800113
// If your ISP provided one or more IP addresses for stable
// name-servers, you probably want to use them as forwarders.
// Uncomment the following block, and insert the addresses replacing
// the all-0's placeholder.
// forwarders {
// 0.0.0.0;
// };
//========================================================================
// If BIND logs error messages about the root key being expired,
// you will need to update your keys. See https://www.isc.org/bind-keys
//========================================================================
dnssec-validation auto;
auth-nxdomain no; # conform to RFC1035
listen-on-v6 { any; };
forward first;
forwarders {
95.169.183.219; // primary VPN service DNS server
89.41.60.38;
37.221.175.198;
};
};
Iptables
To redirect the traffic to the VPN connection we need iptables. We store the following configuration under “/etc/iptable.up.rules”
*nat
:PREROUTING ACCEPT [1:148]
:INPUT ACCEPT [1:148]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
-A POSTROUTING -o tun0 -j MASQUERADE
COMMIT
# Completed on Thu Oct 18 02:22:06 2012
# Generated by iptables-save v1.4.14 on Thu Oct 18 02:22:06 2012
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -i lo -j ACCEPT
-A INPUT -d 127.0.0.0/8 ! -i lo -j REJECT --reject-with icmp-port-unreachable
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -i eth0 -j ACCEPT
#####################################################################################
-A INPUT -i tun0 -p icmp -m icmp --icmp-type 8 -j REJECT
-A INPUT -p icmp -m icmp --icmp-type 8 -j ACCEPT
-A INPUT -m limit --limit 5/min -j LOG --log-prefix "iptables denied: " --log-level 7
-A INPUT -j REJECT --reject-with icmp-port-unreachable
-A FORWARD -i tun0 -o eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -i eth0 -o tun0 -j ACCEPT
-A FORWARD -j REJECT --reject-with icmp-port-unreachable
-A OUTPUT -j ACCEPT
COMMIT
To load the rules on the network start up we write a script under “/etc/network/if-pre-up.d/” which contains the following:
#!/bin/bash
/sbin/iptables-restore < /etc/iptables.up.rules
And we make it belong to the root and executable.
chown root:root /etc/network/if-pre-up.d/iptables
chmod +x /etc/network/if-pre-up.d/iptables
Kernel
To prepare the kernel for IP forwarding we must uncomment the following line in the file “/etc/sysctl.conf” :
net.ipv4.ip_forward = 1
The hardware stuff
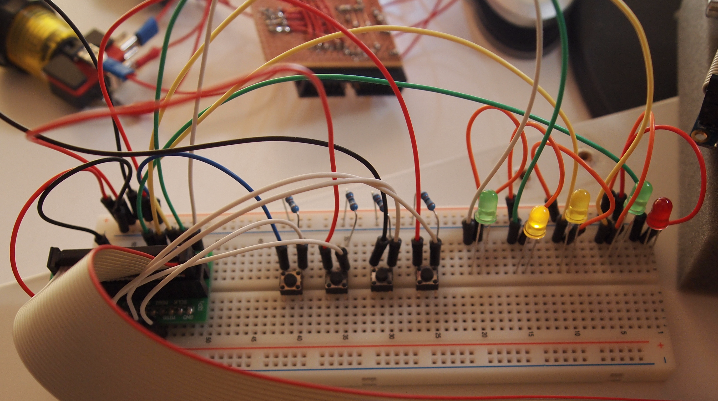

Things that did not work
When I switched the raspberry pi for the more capable banana pi I became a problem with a switch that wouldn’t work. The hardware part was fine and I could even see the button press with the wiringpi tool “gpio” with the “readall” argument. Only Python would not register the edge on the pin 7 and 5. So I have to switch the button to the pin 19.
Obsolete Steps
Squid
I needed this part in an earlyer version where I had problems with hiding my location in Netflix on PC browsers. It seems that this is no longer the case, therefor this part is obsolete but remains here for nostalgic reasons.
Squid is hour proxy server with which I had good results to circumvent the location detection of Netflix. This solution is for my PC which had problems when only using the gateway. The TV for example has no such problems.
This is my config which lies under “/etc/squid3/squid.conf”:
#basic config
http_port 192.168.1.161:3128
cache_mem 256 MB
maximum_object_size 10000 KB
maximum_object_size_in_memory 64 KB
cache_replacement_policy heap LFUDA
memory_replacement_policy heap GDSF
#anonymisation
via off
forwarded_for off
#permissions
acl silvercloud src 192.168.1.0/24
http_access allow silvercloud
You may want to change the ips to reflect your own network. An important block is under anonymisation which hides that the client goes throung a proxy.